Family Safe Computers
Instant Messaging (IM) or better known as Messaging, and Talk Rooms, utilize the Internet as the backbone for their functionality. These services provide instant communication inbetween two user’s computers either through typing messages, sending files, and or even pictures. These communications emerge instantaneously on the recipient’s computer once the sender presses “enter” or selects “send.”
It is significant to make a distinction inbetween the various types of messaging platforms and possibilities.
1. Messaging programs can be found for both computers and smartphones. Computers require a puny program to be downloaded and installed whereas a smartphone user can lightly install an app from the manufacturer’s app store. Either way, these programs require a user to log on and use a designated username (screenname / treat etc.) that becomes their identity on the system while in use. This may seem redundant to mention – but it is significant to understand this type of messaging utilizes the Internet network for transporting the message.
Two. Cell phones (both roll phones and smartphones) can also send text message (SMS = Brief Message Service) to other phones with only the use of a phone number. This messaging service is very plain and built into the phone. The phone service provider (Verizon, Sprint, ATT etc.) produces the message for the user through the cellular network as opposed to the Internet.
Trio. It is entirely possible, and very likely, that users will utilize both the phone carrier’s network to send SMS messages, while also using a messaging app to communicate over the phone’s Internet (data) connection.
Instant Messaging (Messaging)
Instant Messaging (IM or IMing) is a service permitting users to send typed messages, pictures, files, and live movie to a recipient based on their screen name. This exchange can go back and forward as long as both parties desire. It provides a private way of communicating with friends and other known contacts and is very popular among teenagers as well as many adults.
In order to use this service a user must download a free program and install it on their computer or an app for their phone or tablet. There are several available with some of the more popular ones being WhatsApp, Facebook Messenger, QQ Mobile, WeChat, Viber, and even Skype. The old days it was Yahoo Messenger, Windows Live Messenger, and AIM (America Online IM). The program treats all the communication and provides a window for the user to type and receive messages.
Many popular social networking sites like www.Facebook.com suggest messaging as part of the overall platform it offers customers along with many other options. Additionally, companies like Alphabet (Google), Microsoft, and Yahoo suggest membership accounts permitting users to register in exchange for access to web services like e-mail, office programs, document storage, calendar, messaging, and many other resources for free. Once logged into the web site, a user can seamlessly maneuver to all application options. The website also keeps track of user activities in order to provide a personalized practice on come back visits; while also learning about their activities for target marketing. There are no verification efforts to make sure a person creating an account is who they say they are. This permits for an anonymity many predators desire when they can pose as a much junior person in order to meet others.
With this numerous service concept in mind, a teenager who registers for a free Yahoo email account will also have access to all the other features. The individual information listed during the initial registration also becomes part of the teen’s online profile for that service. Therefore it is always significant to think twice before coming in any private information within online profile registration pages. Keep it all generic.
A “buddy list” or “messenger list” is a puny active window inwards an IM program listing screen name contacts a user considers a friend. It permits quick communication by clicking the name and typing a message. Indicators also expose the status of a friend (signed on or not) by placing some type of icon next to the name. It is very common for teenagers to have numerous names in their list. For safety reasons teenagers should set options in their account to only permit contacts from users on their friend or messenger list and never permit files to be accepted on their computer to reduce potential virus threats from a friend’s computer.
Talk Rooms
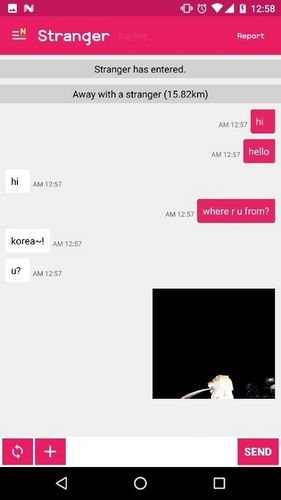
Talk rooms are similar to Instant Messaging, (IM) but unlike direct one-to-one communication, users log on to a themed based virtual room and communicate with a group of users. Participants interact by sending typed messages that all connected users can read and react to like a big online get together. There are numerous talk topics to choose from such as: hobbies, television shows, boy bands, sports, politics, health issues, and relationships. Basically if there is an interest, there is most likely a talk room available. While watching talk room dialog, users will likely notice most postings are just typed advertisements for other web sites and similar items with very few legitimate conversations taking place. It serves more as a place for users to post their name and wait for someone to invite them to a private Instant Message session.
As mentioned above, many talk rooms are seamless with IM services with regard to certain web sites. Once a user has an account they can travel inbetween both worlds with the click of a mouse. “Yahoo Chat” is one example. While using “Yahoo Instant Message” a user can simply drop down a menu and select “Yahoo Chat” and instantly be introduced with a list of available topics and corresponding rooms. Other examples are “AIM Chat” and “Google Hangout.” There are, however, many other talk room web sites that concentrate on talking exclusively and are not tied with major search engine web sites.
A talk room window basically combines people who will only know each other based on their profile and registered screen name. If a person determines they want to “go private” with someone in the room, they click that person’s name and ask to send an Instant Message. At that point, both users are at the same time still in the room while engaging in a private IM session in a fresh pop up window. Predators use this feature to target users they meet in talk rooms. Additionally, once a predator knows a user’s screen name he or she can directly send Instant Messages to that person by simply opening the IM service, typing in the name and message. Many also send direct requests to be added to the other person’s friend or contact list.
IM and Talk Room Do’s and Don’ts
- Attempt it yourself (learn what it is about) – use the service to communicate with your children
- Use generic screen names and profile information so predators cannot use it to gather information. For example screen names like "boytoy17" or "soccrgrl13" are very inviting to predators because the name itself provides an pic into that user’s life (soccrgrl13 it likely a soccer player and either thirteen years old or it’s her jersey number)
- Require children to save IM and talk history for parent review
- Monitor child use (stay involved)
- Set preferences to only permit IM’s from Pal or Messenger List, this blocks messages from users you do not know – especially predators who may attempt to send an IM while in a talk session
- Ask your child about each screen name on their list at least once a week to see how they know that person. If they only know them through online correspondence delete the name.
- No Web Cam. Almost all Instant Messaging services permit movie and audio to be sent through the connected session. If there is no camera on your computer it can’t be used.
- PARENT For Your Information – If you don’t know how to manipulate the above settings ask your children or a friend for help. Anyone with some basic computer practice will likely be able to help you locate where to go. If you still can’t find it, look for words like "preferences", "privacy", or "options" within the program windows.
IM Code
When using IM and talk rooms it is common to use abbreviations for words or phrases that take too much time to type. This type of abbreviating almost becomes a cryptic language of its own preventing unacquainted users from understanding what is actually being typed. This puts parents at a disadvantage even if they are watching over their child’s shoulder. There are even codes for telling others a parent is watching.
IM Code deciphers can be found by searching the Internet or using the following websites:
Keyloggers
These programs record computer keystrokes and operate in the background within the computer device without users knowing. These can be used to see what your children are typing including their passwords. Note. We do not endorse any of the below programs nor do we assure that they are legitimate and we are not liable if used. We are only providing a link to their download page for your consideration.
The information on this site is distributed on an “As Is” basis, without warranty and is not intended to infringe on any copyrighted material or other author’s work product. Family Safe Computers shall not have any liability to any person or entity with the respect to any loss or harm caused or alleged to be caused directly or indirectly by the instructions or concepts contained in the material or by the computer software and hardware products described in it. If you feel material listed in this guide is an infringement of your copyright or work product, or have other concerns about the material listed please contact us.
Messaging – Talk Rooms, Family Safe Computers
Family Safe Computers
Instant Messaging (IM) or better known as Messaging, and Talk Rooms, utilize the Internet as the backbone for their functionality. These services provide instant communication inbetween two user’s computers either through typing messages, sending files, and or even pictures. These communications show up instantaneously on the recipient’s computer once the sender presses “enter” or selects “send.”
It is significant to make a distinction inbetween the various types of messaging platforms and possibilities.
1. Messaging programs can be found for both computers and smartphones. Computers require a puny program to be downloaded and installed whereas a smartphone user can lightly install an app from the manufacturer’s app store. Either way, these programs require a user to log on and use a designated username (screenname / treat etc.) that becomes their identity on the system while in use. This may seem redundant to mention – but it is significant to understand this type of messaging utilizes the Internet network for transporting the message.
Two. Cell phones (both roll phones and smartphones) can also send text message (SMS = Brief Message Service) to other phones with only the use of a phone number. This messaging service is very elementary and built into the phone. The phone service provider (Verizon, Sprint, ATT etc.) produces the message for the user through the cellular network as opposed to the Internet.
Three. It is entirely possible, and very likely, that users will utilize both the phone carrier’s network to send SMS messages, while also using a messaging app to communicate over the phone’s Internet (data) connection.
Instant Messaging (Messaging)
Instant Messaging (IM or IMing) is a service permitting users to send typed messages, pictures, files, and live movie to a recipient based on their screen name. This exchange can go back and forward as long as both parties desire. It provides a individual way of communicating with friends and other known contacts and is very popular among teenagers as well as many adults.
In order to use this service a user must download a free program and install it on their computer or an app for their phone or tablet. There are several available with some of the more popular ones being WhatsApp, Facebook Messenger, QQ Mobile, WeChat, Viber, and even Skype. The old days it was Yahoo Messenger, Windows Live Messenger, and AIM (America Online IM). The program treats all the communication and provides a window for the user to type and receive messages.
Many popular social networking sites like www.Facebook.com suggest messaging as part of the overall platform it offers customers along with many other options. Additionally, companies like Alphabet (Google), Microsoft, and Yahoo suggest membership accounts permitting users to register in exchange for access to web services like e-mail, office programs, document storage, calendar, messaging, and many other resources for free. Once logged into the web site, a user can seamlessly maneuver to all application options. The website also keeps track of user activities in order to provide a personalized practice on comeback visits; while also learning about their activities for target marketing. There are no verification efforts to make sure a person creating an account is who they say they are. This permits for an anonymity many predators desire when they can pose as a much junior person in order to meet others.
With this numerous service concept in mind, a teenager who registers for a free Yahoo email account will also have access to all the other features. The individual information listed during the initial registration also becomes part of the teen’s online profile for that service. Therefore it is always significant to think twice before injecting any private information within online profile registration pages. Keep it all generic.
A “buddy list” or “messenger list” is a puny active window inwards an IM program listing screen name contacts a user considers a friend. It permits quick communication by clicking the name and typing a message. Indicators also expose the status of a friend (signed on or not) by placing some type of icon next to the name. It is very common for teenagers to have numerous names in their list. For safety reasons teenagers should set options in their account to only permit contacts from users on their mate or messenger list and never permit files to be accepted on their computer to reduce potential virus threats from a friend’s computer.
Talk Rooms
Talk rooms are similar to Instant Messaging, (IM) but unlike direct one-to-one communication, users log on to a themed based virtual room and communicate with a group of users. Participants interact by sending typed messages that all connected users can read and react to like a big online get together. There are numerous talk topics to choose from such as: hobbies, television shows, boy bands, sports, politics, health issues, and relationships. Basically if there is an interest, there is very likely a talk room available. While watching talk room dialog, users will likely notice most postings are just typed advertisements for other web sites and similar items with very few legitimate conversations taking place. It serves more as a place for users to post their name and wait for someone to invite them to a private Instant Message session.
As mentioned above, many talk rooms are seamless with IM services with regard to certain web sites. Once a user has an account they can travel inbetween both worlds with the click of a mouse. “Yahoo Chat” is one example. While using “Yahoo Instant Message” a user can simply drop down a menu and select “Yahoo Chat” and instantly be introduced with a list of available topics and corresponding rooms. Other examples are “AIM Chat” and “Google Hangout.” There are, however, many other talk room web sites that concentrate on talking exclusively and are not tied with major search engine web sites.
A talk room window basically combines people who will only know each other based on their profile and registered screen name. If a person determines they want to “go private” with someone in the room, they click that person’s name and ask to send an Instant Message. At that point, both users are at the same time still in the room while engaging in a private IM session in a fresh pop up window. Predators use this feature to target users they meet in talk rooms. Additionally, once a predator knows a user’s screen name he or she can directly send Instant Messages to that person by simply opening the IM service, typing in the name and message. Many also send direct requests to be added to the other person’s pal or contact list.
IM and Talk Room Do’s and Don’ts
- Attempt it yourself (learn what it is about) – use the service to communicate with your children
- Use generic screen names and profile information so predators cannot use it to gather information. For example screen names like "boytoy17" or "soccrgrl13" are very inviting to predators because the name itself provides an photo into that user’s life (soccrgrl13 it likely a soccer player and either thirteen years old or it’s her jersey number)
- Require children to save IM and talk history for parent review
- Monitor child use (stay involved)
- Set preferences to only permit IM’s from Pal or Messenger List, this blocks messages from users you do not know – especially predators who may attempt to send an IM while in a talk session
- Ask your child about each screen name on their list at least once a week to see how they know that person. If they only know them through online correspondence delete the name.
- No Web Cam. Almost all Instant Messaging services permit movie and audio to be sent through the connected session. If there is no camera on your computer it can’t be used.
- PARENT For Your Information – If you don’t know how to manipulate the above settings ask your children or a friend for help. Anyone with some basic computer practice will likely be able to help you locate where to go. If you still can’t find it, look for words like "preferences", "privacy", or "options" within the program windows.
IM Code
When using IM and talk rooms it is common to use abbreviations for words or phrases that take too much time to type. This type of abbreviating almost becomes a cryptic language of its own preventing unacquainted users from understanding what is actually being typed. This puts parents at a disadvantage even if they are watching over their child’s shoulder. There are even codes for telling others a parent is watching.
IM Code deciphers can be found by searching the Internet or using the following websites:
Keyloggers
These programs record computer keystrokes and operate in the background within the computer device without users knowing. These can be used to see what your children are typing including their passwords. Note. We do not endorse any of the below programs nor do we ensure that they are legitimate and we are not liable if used. We are only providing a link to their download page for your consideration.
The information on this site is distributed on an “As Is” basis, without warranty and is not intended to infringe on any copyrighted material or other author’s work product. Family Safe Computers shall not have any liability to any person or entity with the respect to any loss or harm caused or alleged to be caused directly or indirectly by the instructions or concepts contained in the material or by the computer software and hardware products described in it. If you feel material listed in this guide is an infringement of your copyright or work product, or have other concerns about the material listed please contact us.